Port Redirection on VIP with same External and Mapped IP
| Products : FortiGate |
| https://kb.fortinet.com/kb/documentLink.do?externalID=FD45204 |
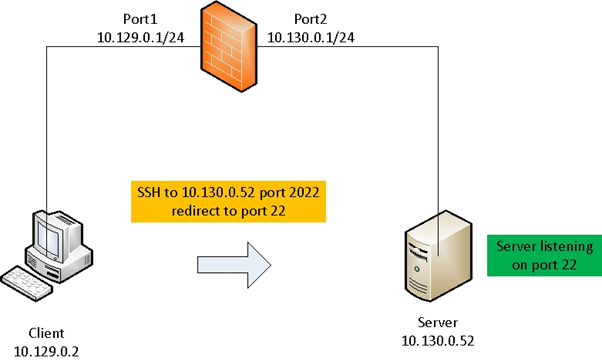
This article describes how to apply port redirection for specific application in VIP when External and Mapped IP addresses are the same.Below is the diagram of a client trying to connect to the application server on port 2022 while the server is listening on port 22, the VIP settings have the same IP for both External and Mapped IP.
What I want to highlight is that does not work in FortiOS 6.2 or FortiOS 6.4
Solution
Create DNAT VIP using CLI and configure the same IP for both External and Internal IP with the required port redirection. Ensure arp-reply setting is disable, else the response will come from the FortiGate interface.
# edit “SSH_redirect”
set extip 10.130.0.52
set extintf “any”
set arp-reply disable <- arp-reply must be disable, else it will hit local-in policy
set portforward enable
set mappedip “10.130.0.52”
set extport 2022
set mappedport 22
nextNext, create a new firewall policy as below by referencing the VIP object:
# config firewall policy
edit 1 set srcintf “port1” set dstintf “port2” set srcaddr “all” set dstaddr “SSH_redirect” set action accept set schedule “always” set service “ALL” end
Debug flow output as below indicate the the traffic have been accepted:id=20085 trace_id=1 func=print_pkt_detail line=5347 msg=”vd-root received a packet(proto=6, 10.129.0.2:50213->10.130.0.52:2022) from port1. flag [S], seq 1249160343, ack 0, win 8192″
id=20085 trace_id=1 func=init_ip_session_common line=5506 msg=”allocate a new session-0000d0c9″
id=20085 trace_id=1 func=fw_pre_route_handler line=185 msg=”VIP-10.130.0.52:22, outdev-unkown”
id=20085 trace_id=1 func=__ip_session_run_tuple line=3268 msg=”DNAT 10.130.0.52:2022->10.130.0.52:22″
id=20085 trace_id=1 func=vf_ip_route_input_common line=2574 msg=”find a route: flag=04000000 gw-10.130.0.52 via port2″
id=20085 trace_id=1 func=fw_forward_handler line=743 msg=”Allowed by Policy-58:”
id=20085 trace_id=2 func=print_pkt_detail line=5347 msg=”vd-root received a packet(proto=6, 10.129.0.2:50213->10.130.0.52:2022) from port1. flag [.], seq 1249160344, ack 3448098817, win 256″
id=20085 trace_id=2 func=resolve_ip_tuple_fast line=5422 msg=”Find an existing session, id-0000d0c9, original direction”
id=20085 trace_id=2 func=__ip_session_run_tuple line=3268 msg=”DNAT 10.130.0.52:2022->10.130.0.52:22″
id=20085 trace_id=3 func=print_pkt_detail line=5347 msg=”vd-root received a packet(proto=6, 10.129.0.2:50213->10.130.0.52:2022) from port1. flag [.], seq 1249160344, ack 3448098817, win 256″
En version 6.0 et supérieur, cette configuration n’est pas autorisée:
FortiGate affiche “Mapped IP must be different from External IP”
Static NAT’s extip should be different from mappedip.
object check operator error, -8, discard the settingCommand fail. Return code 1
L’astuce consiste à configurer la VIP en mode load-balance ! Et ouai !
config firewall vip
edit “test”
set type load-balance <———-
set extip 192.168.3.2
set arp-reply disable <—–
set extintf “lan”
set portforward enable
set mappedip “192.168.3.2”
set extport 10443
set mappedport 443
next
end
Pour la petite histoire, j’ai essayé en mode normal et en mode Central NAT. J’ai essayé avec extip = 0/0, pas mieux.
Par ailleurs, il y a aussi une commande qui a disparu (alors qu’elle existait en 5.4):
Pas de réponse du support sur ce point… mais on a trouvé une solution satisfaisante donc…